 Let’s face it, in recent years, the rapid propagation and uncontrolled use of portable mass storage devices has started to pose considerable security risks to corporations. While being very useful, a simple USB key, and even an iPod, could easily be used to steal data or to introduce viruses and other nasties to your network.
Let’s face it, in recent years, the rapid propagation and uncontrolled use of portable mass storage devices has started to pose considerable security risks to corporations. While being very useful, a simple USB key, and even an iPod, could easily be used to steal data or to introduce viruses and other nasties to your network.
Security researchers have long warned us about the risks associated with portable storage devices and how vital it is for companies do something about them. But before going further, let me ask a question to those of you who are in charge of administrating a network: What is your company doing to minimize those risks?
I’ve heard many proposed answers to this inquery; everything from filling USB ports with epoxy, to disabling them completely via BIOS or by implementing group policies. However, in most situations, people won’t do a thing about them, and if this is the case where YOU work, you really need to do something about the situation.
GFI, a security software company that has long been a favorite of mine, has just come out with a simple, elegant solution to the problem. Their answer is named EndPointScan, and it is a free online service that allows you to check which devices are or have been connected to computers on your network (and by whom).
EndPointScan carries out granular checks across all types of ports – USB, Firewire, Bluetooth, Infrared, PCMIA and Wi-Fi – on all machines. This utility provides complete and thorough information about all portable devices and can scan multiple computers simultaneously. EndPointScan is fully compatible with existing network management or administrative tools such as Active Directory and it will also work on Vista systems.
In my case, the application worked flawlessly - just like all other GFI products I’ve used in the past- and did the job it was designed for perfectly.
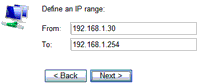 First, before using the tool, you’ll need to install its ActiveX component. Then, a Web interface will ask you about what computers you want to scan: a single machine or a range (or list) of them. It will then proceed to scan your network based on the chosen settings.
First, before using the tool, you’ll need to install its ActiveX component. Then, a Web interface will ask you about what computers you want to scan: a single machine or a range (or list) of them. It will then proceed to scan your network based on the chosen settings.
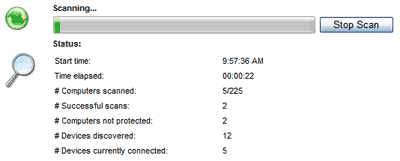
When finished, the application will display a report providing details about which computers may be at risk, and when expanded, will list the devices that are or have been connected to them. Here is a picture of a sample report.
Globally, I must say that I was pretty impressed by the ease of use of this application and the level of information it brought me. Even if EndPointScan will not prevent people from using USB devices on your network, it will at least paint you a good portrait of what is happening in your environment.
 Hmm… I wonder what the application will detect if I ever feel like connecting one of those USB humping dogs to my box. Will it be considered as a security risk? Maybe someone from GFI will eventually end up here and provide us with an answer.
Hmm… I wonder what the application will detect if I ever feel like connecting one of those USB humping dogs to my box. Will it be considered as a security risk? Maybe someone from GFI will eventually end up here and provide us with an answer. ![]()
- [GAS] Giveaway: Free GFI T-Shirts and Frosted Mugs
- Articles and Reviews
- Scan your servers for the SANS top 20 Internet security attacks
- Sony rootkit fiasco: When history repeats itself
You Might Also Like :






0 comments:
Post a Comment